Night Lion Can Help Monitor For Data Leaks And Exposures Of Data From Leaky Servers And Databases.
More than just monitoring data dumps and leaked credentials, Shadowbyte also monitors public NoSQL databases and buckets for sign of information pertaining to your company or brand. Learn how our watchlist can integrate directly with your SOC for realtime alerting.
The Benefits of Shadowbyte
Data Leak Detection
Track threat actor communications across hundreds of forums, private chat channels and paste site to understand their current and historical movements.
Fraud and Abuse Investigation
Prevent insider threat attacks by monitoring forums and private channels where criminals collaborate and plan their attacks.
Data Breach Discovery
Understand the exposure of your 3rd party organizations, or M&A targets, and how that can directly impact your organization.
Stop Password re-use and account takeover attacks
REDUCE THE RISK OF A DATA BREACH BY IDENTIFYING HOW YOUR EMPLOYEES ARE BEING TARGETED.
The fastest way hackers compromise a network is to target common and re-used passwords. As more sites are breached, the available pool of passwords and other identifiable information on your employees increases, which hackers use to mount an attack against your organization.
Reduce the risk of data breach and insider threat
REDUCE THE RISK OF A DATA BREACH BY IDENTIFYING HOW YOUR EMPLOYEES ARE BEING TARGETED.
Attacks are planned in closed-source locations. Access to these forums and private channels will give you direct visibility into when and how your brand is people or company will be targeted. Monitor for Early Signs of Fraud, Insider Threat, and messages with malicious intent.
Early FraudDetection
ADVANCED KEYWORD MONITORING FOR YOUR EMPLOYEES, EXECUTIVES, AND COMPANY BRANDS
Monitor for mentions of keywords and relevant search terms across petabytes of private databases, breached credentials, data leaks, closed-source hacker forums, chat channels, and private darkweb markets, to know the moment information on your company or employees leaks, goes on sale, or is being mentioned in places where it shouldn’t be.
A large majority of At least 44 million corporate accounts are vulnerable to account takeover due to compromised or stolen passwords
Account takeover caused by stolen and re-used passwords make up the cause for a large majority of data breaches over the past four year.
— Microsoft, 2020
Access the largest collection of private hacker data available
24/7 Dark Web Monitoring
Account Takeover Protection

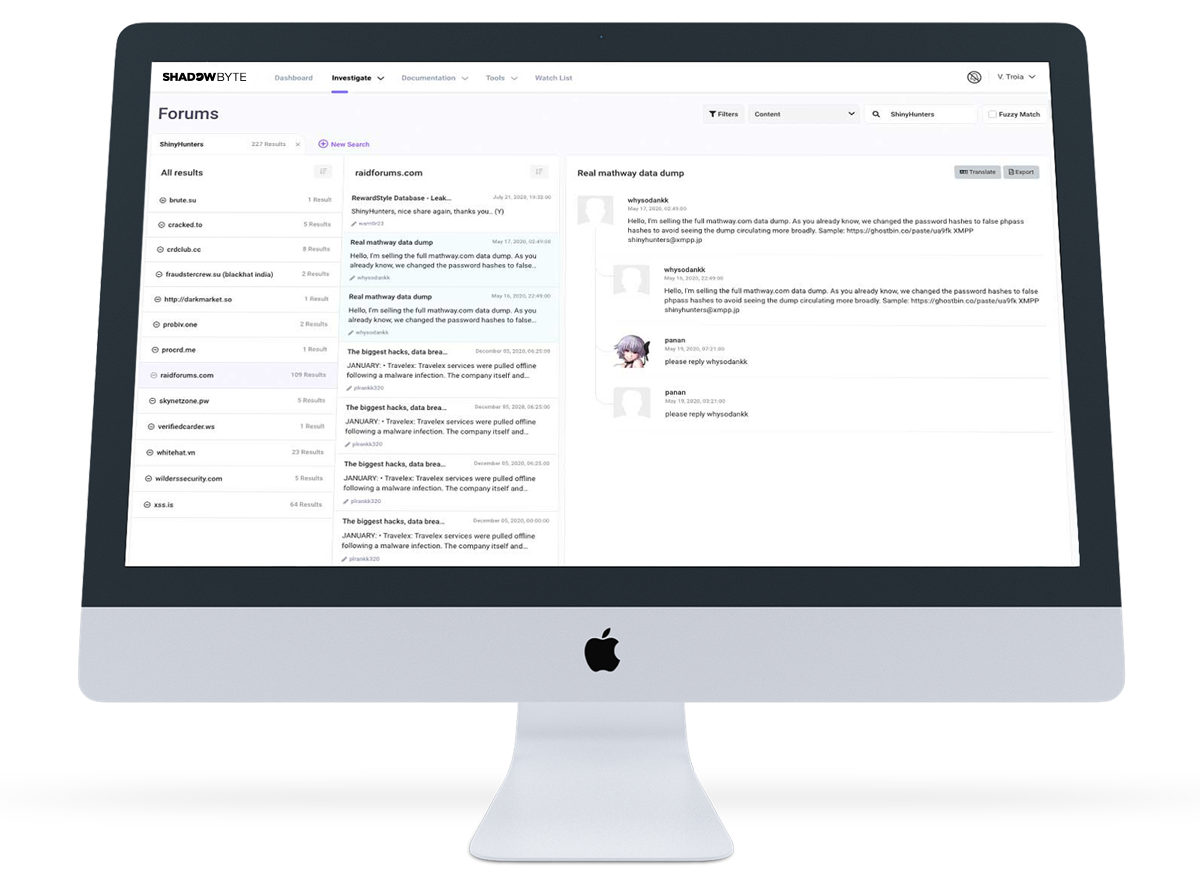
Automated Threat Actor Analysis and Discovery
Case Study
University
Shadowbyte's visibility into private hacker communications provided intelligence necessary to stop a data breach before it even started.


