Advanced Counterintelligence Services
Night Lion Security’s Tailored Threat Intelligence and Investigative Research Services Combined with the Power of Shadowbyte.
Threat Actor Research and Investigation Services
Cyber Criminal Investigations
Assisting with fraud and cyber criminal investigations for organizations and international law enforcement agencies.
Threat Actor Profiling & Attribution
Advanced threat actor research and attribution.
Counterintelligence Services
Extreme thinking often prevails when trying to catch advanced threat actors. Read about our proven track records for more information.
Extortion and Ransom Negotiations
Proven threat actor negotiations and reduced settlements in ransomware and extortion cases.
Grand Jury & Litigation Support
Expert witness testimony and evidence discovery in support of local and Federal Grand Jury cases.
Unrestricted Access
Our threat intelligence agents regularly acquire and maintain access to most exclusive forums and chat rooms where cyber crime is planned.
ShinyHunters Is a Hacking Group on a Data Breach Spree
In the first two weeks of May, they’ve hit the dark web, hawking 200 million stolen records from over a dozen companies.
We wrote the book on Hunting Cyber Criminals and Digital Investigations

Ranked #1 On Amazon’s Top IT Books
Written by Night Lion Security CEO, Vinny Troia, Hunting Cyber Criminals provides an actual account of the author’s experiences during his investigation of TheDarkOverlord and ShinyHunters cybercriminal hacking groups. The book provides a mix of story and technical guides which explore the tools, techniques, and thought processes using during an active cyber terrorist investigation.
Have questions? We are ready to schedule your free consultation
Access the largest collection of private hacker data available
24/7 Dark Web Monitoring
Account Takeover Protection

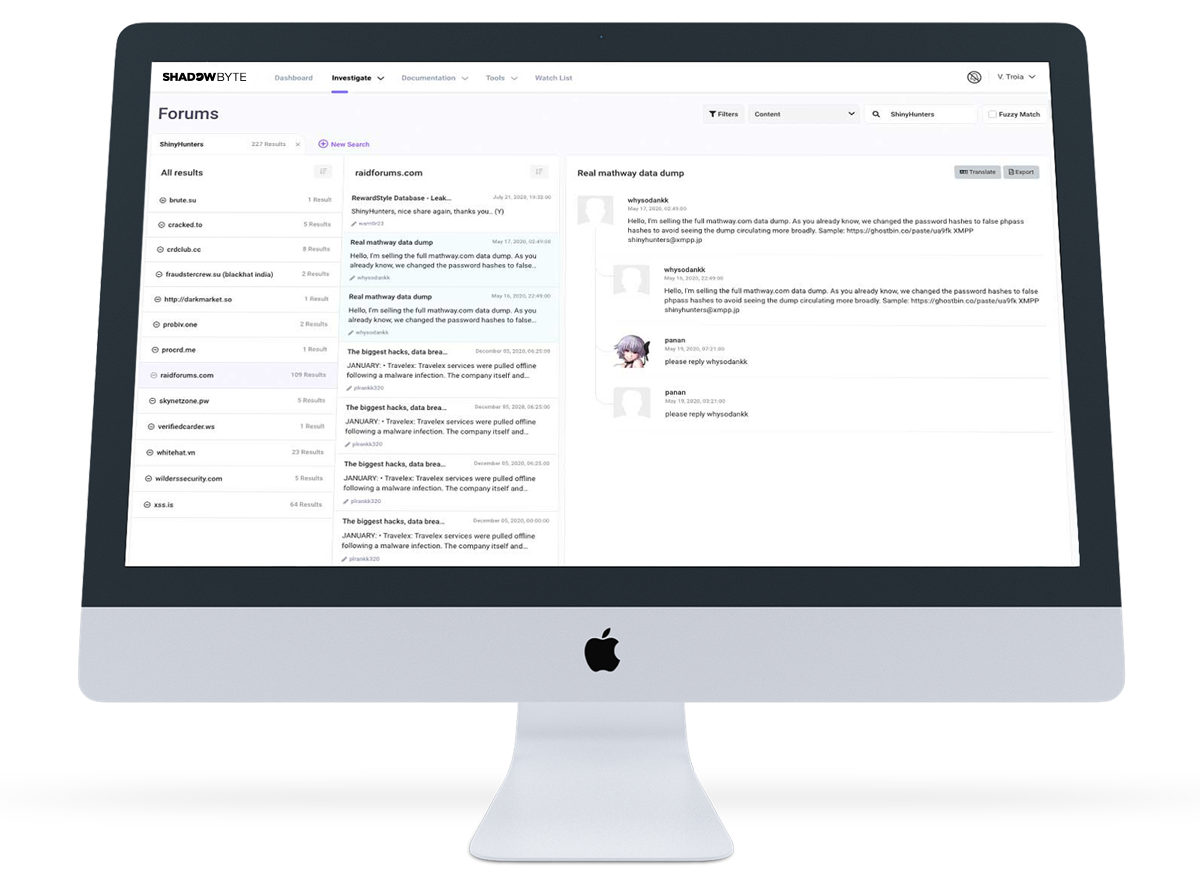
Automated Threat Actor Analysis and Discovery
Case Study
Social Media
Helping a social media giant identify stolen account vendors and take down leaked databases containing sensitive customer information.

Search Across Thousands of Open Databases.
Shadowbyte now has the power to allow you to search and alert across thousands of open Elasticsearch, MongoDB, and NoSQL databases. There are nearly one hundred thousand public databases accessible by anyone, often containing leaked or stolen data!
IN THE MEDIA
Bloomberg interview with Founder Vinny Troia

HLN

CBS News

GMA

Howard Stern

Fox Business

Fox News

AJAM

NBC News

ABC News


