Updated: April 05, 2022.
On November 13, 2021, the FBI.gov domain was used to send out hoax emails to tens of thousands of people regarding Night Lion’s ongoing investigation into The Dark Overlord hacking group. The purpose of the email was to apparently discredit Night Lion & Shadowbyte’s founder, Vinny Troia, claiming that I am a member of that group.
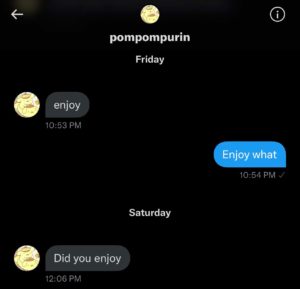
I was initially warned of the attack around 10 pm EST on November 12 when user PomPompurin contacted me via direct message on Twitter to say “Enjoy”. I knew immediately an attack was coming as he typically likes to (sadistically) give me a heads-up right before they stage some sort of attack on me.
A Brief History of My Experience Dealing with Pompompurin
The last time this happened he sent me a message informing me that the National Center for Missing and Exploited Children posted a blog naming me as a sexual predator. Before that it was a heads up on a DDOS attack on our free consumer Breach Check website; before that hacked my personal Twitter using a private API key that was stolen from our Shadowbyte website, in order to send out a number of childish Tweets to reporters; before that he tried to publicly frame me for the hack on Astoria company; and before that, it was something else.

This all started about a year ago when we initially published our cybercrime report naming Christopher Meunier, 22, of Calgary, Canada, as the alleged mastermind behind several major hacking groups including The Dark Overlord, Gnostic Players, and Shiny Hunters.
The report also went on to mention that under his leadership (and impressive hacking skills), his groups were responsible for nearly 40% of all non-credit card-related data breaches over the past 4 years.
PomPompurin claims ownership of the FBI hack
Not surprisingly, PomPompurin contacted Brian Krebs, giving him an exclusive tell-all interview where he described exactly how he hacked and utilized the FBI’s Criminal Justice Information Services (CJIS) servers to carry out his own personal vendetta.
In his interview, PomPompurin describes the method he used to identify multi-factor authentication credentials improperly stored in a browser’s web session – incidentally, this was the same method used by an actor claiming “revenge” after compromising our Shadowbyte honeypot servers last year.
Attribution of Christopher Meunier as PomPompurin
In this instance, the attribution of Chris’ involvement in the PomPompurin group is incredibly simple and straightforward. PomPompurin recently left a critical clue in several of his leaked databases that allowed us to create a straight line back to Meunier.
A brief History of Chris and Whitepacket.
When I first met Chris, I had no idea he was involved in any of these groups. I contacted him in 2018 after he was referred to me by a mutual reporter/friend claiming he had incredible skills as a white hat hacker. At the time, Chris’ website, White Packet Security, also listed him as providing white hat ethical hacking services.
My first conversation with Chris was over XMPP where he used the name whitepacket@xmpp.is – the same XMPP address listed alongside his email address chris@whitepacket.com, both listed as the author/contact for the ZLO Botnet https://github.com/dinamsky/ZloBot on Github.
During our chat, Chris was incredibly hostile and un-trusting. It was a very unusual first conversation to have with someone, and it wasn’t until that time that I realized he was involved in The Dark Overlord group.
At the end of our chat, he directed me to his domain, og.money, after politely telling me to “suck a dick”.
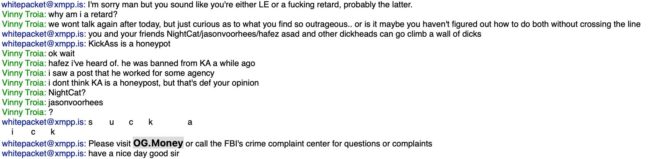
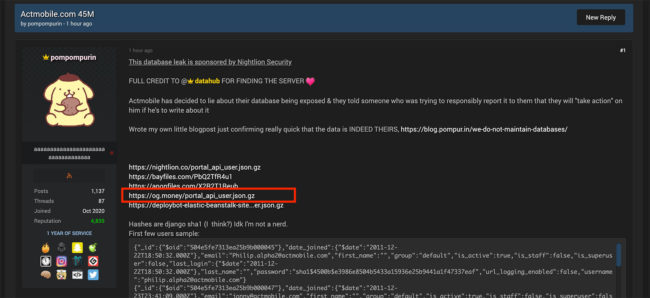
OG.Money used to host Pompompurin’s leaked databases
Tl;DR – a domain used by Meunier in 2018, which shares an IP address for his company WhitePacket.com, is now being used to host PomPompurin’s stolen data.
What is OG.Money?
The OG.money website is labeled as the official website for the hacking group “Money Team”.
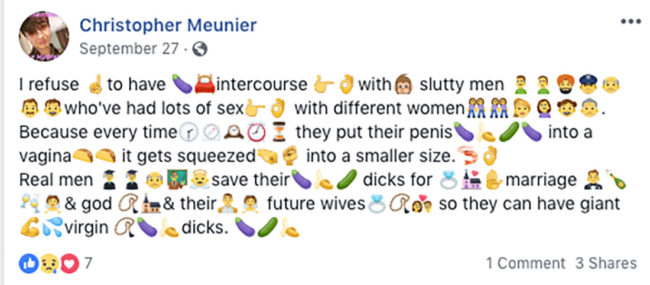
Back in 2018, the website just re-directed you to a “RickRoll” (a video of Rick Astley’s “Never Gonna Give You Up”). At the time, Og.Money was also listed on Meunier’s personal Facebook page, under the username: snoowp.dowgg.3. The following is a screenshot from that personal Facebook page.
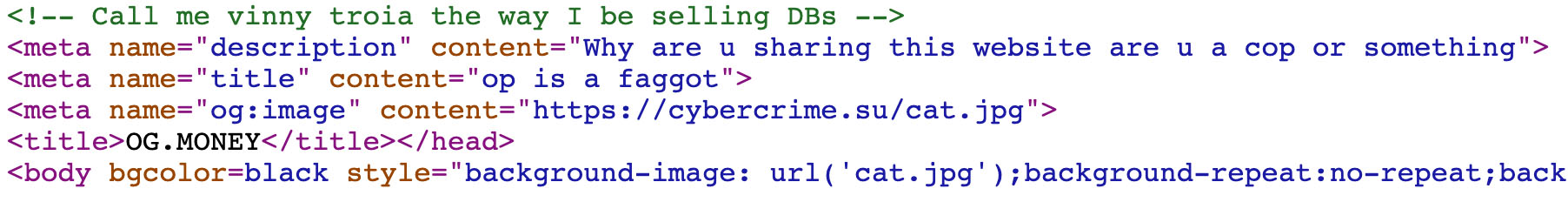
Examining the OG.Money Source Code
Inspection of Og.Money’s source code reveals a personal message to me, as well as another self-deprecating comment referring to the owner of the site as a “faggot”.
In this screenshot, the domain used to host the cat background image is cybercrime.su. This will be important in the next section.
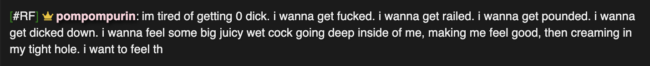
Also worth noting, Chris’s online accounts and activities show a clear pattern of self-deprecating homosexual comments about himself. More about this in my book, Hunting Cyber Criminals.
Attribution for Og.Money
Unfortunately, registration for the og.money domain is private, but according to DomainTools, Og.Money was first registered in 2016 and appears to have never changed hands. However, we can still make a number of inferences based on surrounding evidence.
- Og.Money was originally registered with name.com and used Cloudflare for its DNS. The cloudflare servers on the account during this time were rocky.ns.cloudflare.com and rafe.ns.cloudflare.com.
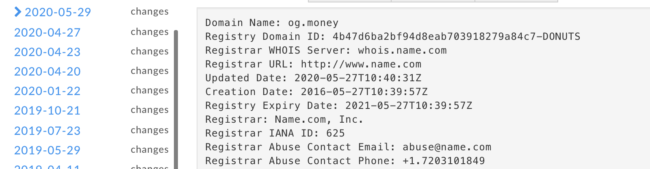
Domain Name: og.money Domain ID: 4b47d6ba2bf94d8eab703918279a84c7-DONUTS WHOIS Server: whois.name.com Referral URL: http://www.name.com Updated Date: 2016-06-06T02:52:39Z Creation Date: 2016-05-27T10:39:57Z Registry Expiry Date: 2017-05-27T10:39:57Z Sponsoring Registrar: Name.com, Inc. Sponsoring Registrar IANA ID: 625 Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited ... Name Server: rocky.ns.cloudflare.com Name Server: rafe.ns.cloudflare.com DNSSEC: unsigned
- The following screenshot from May 2020 shows that OG.Money was first registered in 2016 and does not expire until May of 2021.
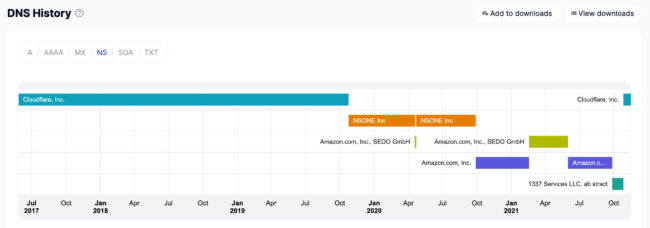
- This chart from SecurityTrails shows the domain’s DNS history with no gaps in ownership going back to 2017.
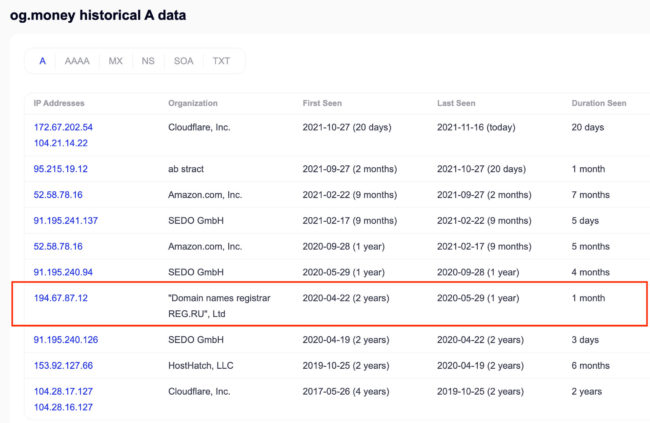
- The following is a list of all the historical IP addresses associated with OG.money. For one month starting April 22, 2020, the domain was hosted on reg.ru and had an IP address of 194.67.87.12.
Connecting Og.Money with Whitepacket.com
The following information will link the domain Og.money with WhitePacket.com (Chris’ official company website).
- In 2017, the domain whitepacket.com was also registered with name.com and used cloudflare for its DNS.
The cloudflare DNS servers were the same ones being used with OG.money

- The following is a historical screenshot of WhitePacket.com (courtesy of Archive.org) which shows the domain forwarding to Meunier’s Twitter account @whitepacket.

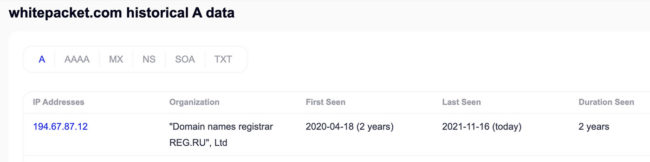
- On April 20, 2020 (four days before og.money), Securitytrails shows Whitepacket.com being transferred to reg.ru, with the same IP address of 194.67.87.12. Whitepacket.com is still hosted on the same IP address.
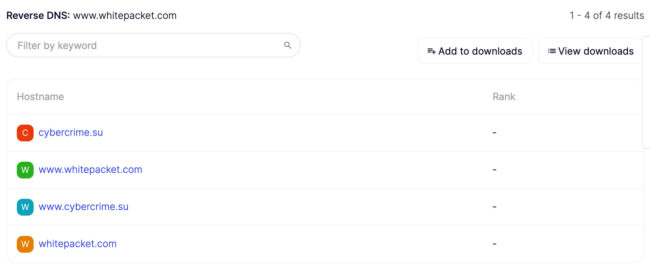
- Finally, the Reverse DNS for 194.67.87.12 shows whitepacket.com hosted on the same server as cybercrime.su (the domain hosting the picture of the cat for og.money).
 \
\
Connecting Pompompurin to Og.money and Meunier
On November, 2021, user PomPompurin uses the domain Og.Money to leak the ActMobile / FreeVPN database, which contains username, passwords, and personal IP addresses of 45 million+ users.
Og.money was moved to Cloudflare at the beginning of this month. Pompompurin has since used the domain to host other database leaks.
A personal Conversation with PomPompurin: The Icing on the Cake.
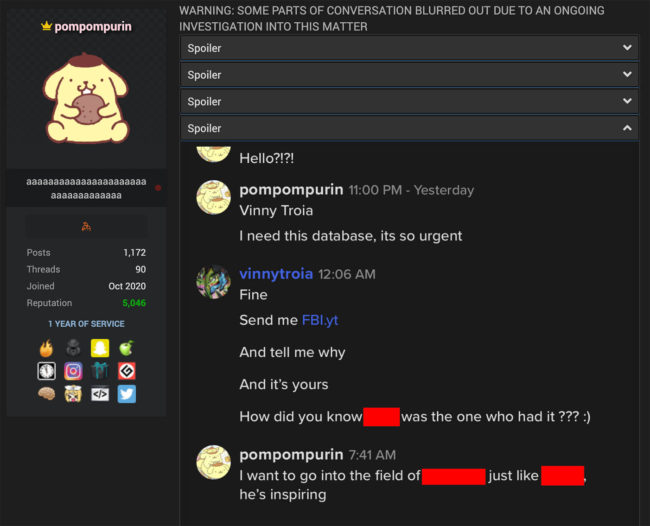
PomPompurin often messages me on various platforms. The following is a screenshot of a conversation he and I had on May of 2021. PomPompurin uploaded this screenshot to Raidforums to insult me, but the version he uploaded was intentionally redacted.
The reason this conversation is significant is because of the information he provided about his childhood friend and hacking partner “Dion” (Dionysius “Dennis” Karvouniaris, aka Ping aka Photon aka NSFW).
There were many conversations that I had with Dion where he talked about getting out of IT/computers completely and going to school for a completely different field. He would never tell me which field, and it was always an unanswered question for me.
Only someone who personally knew Dennis would have understood who I referred to when I said “Dion”. More importantly, Pom provided an answer to a question that no one else could have known. How else could Pompompurin have known that Dion is in Medical school practicing to become a doctor?
And in telling me, he confirmed his identity and (once again) threw his childhood friend under the bus.
Will the FBI finally close this case?
Until now, for reasons unknown to me, the FBI has (apparently) been unable to extradite Meunier. The cyber laws in Canada are very different, and Chris is somehow protected in his perch in Calgary. Perhaps now that the FBI has been victimized and publicly embarrassed by this incident they will have the motivation and urgency to finally take him down.
April 2022 Update: The Identity of Meunier & Pompompurin
In response to several media inquiries regarding the true identity of the person using the Pompompurin Twitter account: No, I do not believe Meunier is the user of the Twitter user Pompompurin. I believe the name PomPompurin is a meme designed to shift attention away from the real hackers.
As I have said in the past, both in published reports and my book, Hunting Cyber Criminals, (which was #1 on Amazon’s technical bestseller list): I believe Meunier’s M.O. is to use a patsy to take the credit for his hacks. I believe that he, and possibly one other person, are responsible for the actual hacking, while a less intelligent (and most likely underage) hacker takes all the credit, gains the notoriety, and eventually takes the fall for the crimes.
NIGHT LION SECURITY
Night Lion Security was founded by Vinny Troia to provide discreet pre- and post-breach security services, including penetration testing, IT audit, and digital forensic investigations. Troia holds a Ph.D. in cybersecurity and is a published author of “Hunting Cyber Criminals”, a book on digital investigations and threat intelligence. In 2020, Hunting Cyber Criminals went to #1 on Amazon’s top networking books.